
throughout the Internet. The origin and authenticity from the file acquired might be checked by digital signatures or by MD5 or other information digests. These easy features with the Internet, more than a throughout the world basis, are switching the creation, sale, and distribution of everything that may be lessened to a pc file for transmission. This consists of all fashion of print publications, program items, information, tunes, film, online video, images, graphics and the other arts. This consequently has triggered seismic shifts in Each and every of the present industries that Formerly managed the production and distribution of such items.}
Figuratively Talking, applications sit in addition to units computer software mainly because they are struggling to operate with no working procedure and system utilities.
Some cafe facts In this particular support are furnished by people. Places to eat can edit information on cafe web page by registering (cost-free).
03:05On cam: Person hurls abuses at governing administration university teacher in MP's Chhatarpur district157 views299 days back
ordinarily audio??material|materials|content|substance|product} is downloaded and performed back on a computer or shifted to a conveyable media participant being listened to around the move. These methods employing very simple gear enable any person, with very little censorship or licensing Command, to broadcast audio-Visible substance worldwide. Electronic media streaming increases the demand for community bandwidth. Such as, standard graphic quality requirements 1 Mbit/s backlink pace for SD 480p, HD 720p top quality demands two.five Mbit/s, and the very best-of-the-line HDX good quality demands 4.five Mbit/s for 1080p.[92]|Webopedia, your on the web tech source, simplifies complicated IT and Personal computer science concepts as a result of conveniently digestible definitions, guides, and opinions. Our aim is always to bridge the information gap by connecting curious minds with the ideal methods, irrespective of their technical qualifications.|Identity and Entry Management In a very latest analyze by Verizon, sixty three% of your confirmed facts breaches are resulting from both weak, stolen, or default passwords made use of.|It truly is pushed by many entities including the Actual physical and tangible components that we are able to contact or sense, called the Hardware and|URIs symbolically discover companies, web servers, databases, along with the paperwork and resources that they can provide. HyperText Transfer Protocol (HTTP) is the leading access protocol on the World-wide-web. Website providers also use HTTP for conversation involving software program programs for details transfer, sharing and exchanging business enterprise data and logistics and is among lots of languages or protocols that may be utilized for interaction on the Internet.[87]|File sharing is definitely an example of transferring large quantities of details over the Internet. A pc file may be emailed to consumers, colleagues and pals being an attachment. It may be uploaded to a website or File Transfer Protocol (FTP) server for easy download by Some others. It might be set right into a "shared spot" or on to a file server for fast use by colleagues. The load of bulk downloads to a lot of people is often eased by the usage of "mirror" servers or peer-to-peer networks. In any of these cases, access to the file could possibly be controlled by user authentication, the transit from the file around the Internet can be obscured by encryption, and dollars may well adjust fingers for access to the file.|The payroll software calculates all unique payment selections and generates the appropriate paychecks. Employee income slips can be printed or sent making use of this software.|Computer software and its Types Computer software is a set of Guidelines, information, or Pc courses that are accustomed to run equipment and carry out specific pursuits.|Contributors to those programs, who could possibly be compensated staff, associates of a corporation or the public, fill fundamental databases with articles applying editing web pages designed for that goal though informal people watch and look at this articles in HTML form. There may or may not be editorial, acceptance and stability programs constructed into the process of using newly entered material and making it available to the concentrate on visitors.|The scenes switch from periods of contentment to instances of terror and unhappiness as the conflict reaches the Female?�s neighbourhood. The fighting forces her and her family members to flee, and soon after time expended over the operate having difficulties to uncover food and escape the chaos, she ultimately winds up inside of a makeshift clinic. The Motion picture shifts from playful, satisfied, and joyful to fearful and unhappy, in underneath two minutes.|Though it has only two camera lenses, the Pixel 9?�s photo processing is borderline magical. It provides new Picture capabilities for instance Add Me, which makes use of a combination of AI and AR to get group pics without having a tripod or some other person taking pictures photographs, and Reimagine, which lets you manipulate photos by introducing fireworks or mountains, say, or modifying colours making use of Google?�s Magic Editor software. The Pixel nine also involves our favourite Pixel eight characteristics: Ideal Choose, which helps you to create a composite Image from a number of photos to grab the top faces out of your topics, Magic Eraser, which may take away distractions and unwelcome qualifications objects in photographs, Audio Magic Eraser, which removes undesired noise from your video clips, Connect with Display screen, which tells you who?�s calling you and what they need before you decide to pick up, and assistive options for instance Guided Frame as well as Magnifier application for people who are blind or have very low eyesight.|Personal computers and routers use routing tables within their functioning program to direct IP packets to succeed in a node on a different subnetwork. Routing tables are preserved by manual configuration or routinely by routing protocols. Finish-nodes ordinarily utilize a default route that factors towards an ISP supplying transit, although ISP routers use the Border Gateway Protocol to ascertain the most effective routing through the complex connections of the global Internet.|Each and every Internet site has its Domain name as it is difficult for anyone to normally remember the long numbers or strings. So, whenever you look for any domain name from the search bar on the browser the ask for are going to be despatched for the server Which server will seek to find the IP tackle with the Area identify as it simply cannot comprehend the area identify.|As well as getting transmitted from person to person, bacterial bacterial infections can also be transmitted through the Chunk of the contaminated insect. Also, consuming contaminated food stuff or h2o may produce an an infection.|Cyber Crimes: Cyberbullying, spam, viruses, hacking, and stealing information are a number of the crimes which can be within the verge lately. Your technique which incorporates all of the private data can be conveniently hacked by cybercriminals.|¡El amor no da dinero! La historia del ?�Estafador de Bumble??que ha engañado a más de 70 mujeres|Packet Seize Appliance intercepts these packets as they are touring from the network, so that you can look at their contents working with other systems. A packet capture is definitely an information accumulating Device, but not an analysis Resource. That's it gathers "messages" but it does not evaluate them and work out what they signify. Other plans are required to execute targeted traffic analysis and sift by way of intercepted information on the lookout for crucial/practical details. Under the Communications Help For Regulation Enforcement Act all U.S. telecommunications providers are needed to put in packet sniffing technological know-how to allow Federal regulation enforcement and intelligence companies to intercept all of their prospects' broadband Internet and VoIP site visitors.[170]|Whilst you'll commonly pay back a lower price to the phone upfront compared to an unlocked phone, you'll need to conform to an extended-phrase agreement to remain on their own community and keep having to pay them for their expert services. At the time your contract is fulfilled, some carriers might enable you to unlock your phone. This, on the other hand, doesn't assure your phone will likely be suitable Together with the provider of the decision.}
You can do a surprising degree of Focus on an iPad with the best gear. These are the best components for turning your iPad into a mobile do the job Place.
Bullying and Spreading Negativity: The Internet has offered a no cost Device in the shape of social websites apps to all those people who normally make an effort to distribute negativity with really revolting and shameful messages and take a look at to bully each other and that is Improper.
When people today contribute helpful and appropriate facts, they earn respect, which makes the sharer come to feel fantastic about them selves.
When the World wide web created while in the nineties, a normal Web content was stored in accomplished sort on an internet server, formatted in HTML, All set for transmission to an internet browser in reaction into a request. After a while, the entire process of developing and serving Websites is becoming dynamic, making a flexible style, layout, and content material. Web sites are frequently made working with information management computer software with, originally, little or no content material.
It operates the newest version of Android with nearly 5 years of protection updates, and it supports 5G, so it works on all three important carriers.,??16|sixteen}??The practice of dividing a community into two or maybe more networks is called subnetting. Computers that belong to a subnet are dealt with with A similar most-sizeable little bit-group in their IP addresses.|Applications can be employed commonly for cellular gadgets whereas Applications can be termed to be a software program software for doing a chosen job.|The iPhone sixteen has a quick processor for far better gaming general performance (and AI functions, which get started rolling out subsequent month). In addition it gains the customizable Action button that was reserved for the professional models previous calendar year, a Camera Regulate button for immediately taking images, all-working day battery lifestyle with quickly charging, in addition to a redesigned rear camera method by using a new ultrawide lens for capturing in-depth macro photos.|Social Networking: The purpose of social networking web sites and apps is to attach persons everywhere in the earth.|Observe A computer is usually a piece of Digital equipment. Because it is run by electrical energy, it really is often called an Digital machine. It accepts details, procedures it, and outputs the right effects. The output of a pc process is generally known as the results of the pc process.|Electronic Evidence website Collection in Cybersecurity In the early 80s PCs became more popular and simply obtainable to the overall inhabitants, this also led on the improved usage of desktops in all fields and felony pursuits have been no exception to this. As A lot more Computer system-connected crimes began to area like Computer system frauds, application cracking|Whenever a microorganism is cultured, it allows your health care provider to establish what?�s triggering your situation. In the situation of a bacterial an infection, it could also assist them select which antibiotic could be helpful in managing your problem.|So after obtaining the IP address, the browser will move on the even further ask for to your respective server and now the server will procedure the ask for to Show the articles of the website which the client wants. For anyone who is using a wireless medium of Internet like 3G and 4G or other cellular details then the data will start out flowing in the optical cables and can first achieve towers from there the alerts will reach your cell phones and PCs by means of electromagnetic waves and When you are utilizing routers then optical fiber connecting to the router might help in connecting those mild-induced indicators to electrical indicators and with the assistance of ethernet cables internet reaches your desktops and therefore the necessary data. |Encapsulation is eradicated by the receiving host. Intermediate relays update website link encapsulation at Every single hop, and inspect the IP layer for routing uses.|Critical Management in Cryptography In cryptography, it is an extremely monotonous activity to distribute the public and private keys between sender and receiver.|On-line Banking and Transaction: The Internet enables us to transfer money online in the Web banking technique. Funds may be credited or debited from a single account to another.|What's Venture Management Software? A challenge is described for a series of routines, structured tasks, and deliverables that are diligently executed to obtain a ideal final result Therefore.|The video concludes with the interviewer permitting the interviewees in within the prank. He explains there are presently many billions of folks all through the globe who will be undertaking the exact same career ??mothers|moms}.|A programmed set of Guidance used to accomplish a presented job is generally known as computer software. Users are not able to begin to see the application. Users are only capable to appreciate and validate their features.|?�No quiero perder mi trabajo?? trailero sufre accidente y llora desconsolado; la empresa le responde|The Internet and the online Introduction : The internet is a global network of interconnected desktops and servers that permits persons to communicate, share details, and obtain sources from wherever in the world.|Buffer Overflow Attack with Illustration A buffer is A short lived area for info storage. When extra information (than was initially allotted being saved) receives placed by a system or technique system, the extra knowledge overflows.|When you've got currently registered for any PIN, chances are you'll review or update your current application utilizing the button below|IPv6 is indirectly interoperable by style and design with IPv4. In essence, it establishes a parallel Variation from the Internet indirectly available with IPv4 program. Thus, translation facilities need to exist for internetworking or nodes have to have copy networking software program for the two networks. Effectively all modern Personal computer running units support the two variations on the Internet Protocol.|Simulation Application: Simulation Software package is usually a style of Software that is used to match two unique styles of solutions and likewise it helps in evaluating them.|03:08On Cam: Crane drags automobile with senior citizens sitting down within, scenario registered | movie goes viral670 views268 days back|Zero-rating, the observe of Internet assistance companies allowing buyers cost-free connectivity to access precise material or applications without the need of Value, has provided prospects to surmount economic hurdles but has also been accused by its critics as making a two-tiered Internet. To deal with the issues with zero-score, another model has emerged while in the concept of 'equal ranking' and it is staying analyzed in experiments by Mozilla and Orange in Africa.|Cybersectarianism is a fresh organizational sort that involves, "extremely dispersed modest teams of practitioners which will stay mostly anonymous in the larger sized social context and operate in relative secrecy, although even now connected remotely to a bigger community of believers who share a list of techniques and texts, and infrequently a standard devotion to a selected chief. Abroad supporters deliver funding and assistance; domestic practitioners distribute tracts, take part in acts of resistance, and share information on the internal scenario with outsiders.|The facial expression observed when somebody watches one thing thrilling is similar facial expression observed when faced with a fight or ?�flight??(operate) survival come upon.|An ISP could use just one upstream supplier for connectivity, or apply multihoming to attain redundancy and load balancing. Internet Trade factors are significant website traffic exchanges with physical connections to several ISPs. Large corporations, which include tutorial establishments, huge enterprises, and governments, could execute the identical perform as ISPs, partaking in peering and paying for transit on behalf in their inner networks. Research networks usually interconnect with substantial subnetworks for example GEANT, GLORIAD, Internet2, as well as the UK's countrywide investigation and training community, JANET.}
Substitution Cipher Hiding some data is known as encryption. When plain textual content is encrypted it becomes unreadable and is known as ciphertext. 5G goods in this manner goes from the conditions of service. We recommend employing hotspot or knowledge designs to obtain RV internet if you wish to go the cellular route.|You may affirm the protection by making use of a zip code map furnished by the provider. Alternatively, request Your loved ones or close friends how perfectly their phones work in a certain location.|Psychological Profiling in Cybersecurity The Cybersecurity Profiling is about trying to keep the pc methods Protected from your poor peoples who want to steal the data or can cause damage.|Programs application contains lower-degree plans that interact with the pc at an incredibly standard amount. This features working systems, compilers, and utilities for taking care of Laptop resources.}
nonetheless it?�ll set you back.|Personal computer Forensic Report Structure The most crucial target of Computer system forensics is always to perform a structured investigation over a computing gadget to understand what occurred or who was responsible for what occurred, though protecting a correct documented chain of proof in a proper report. Syntax or template of a Computer Forensic Report is as fo|Convenience to individuals: With out Placing any Actual physical work you are able to do so a lot of things like shopping online it may be anything from stationeries to clothing, guides to private items, and so forth. You are able to textbooks teach and aircraft tickets online.|Delivers mother or father locator and paternity institution services, and also support to determine and implement child and/or health care support orders and selection and distribution of child help payments|Implementation of Diffie-Hellman Algorithm Diffie-Hellman algorithm:The Diffie-Hellman algorithm is getting used to establish a shared solution that can be useful for magic formula communications even though exchanging data above a community network using the elliptic curve to make details and acquire The trick vital utilizing the parameters. For your sake of simplicity|Closed supply: This group includes nearly all the application software plans used currently. These are generally Ordinarily billed, and the source code is often shielded by mental assets rights or patents.|Satellite internet companies like HughesNet and Viasat present internet usage of ninety nine% of America, so Even though you?�re in really hard-to-reach areas, you can get broadband internet velocity.|A viral illness is any situation that?�s a result of a virus. There are plenty of sorts of viral disorder, depending upon the fundamental virus. We?�ll go more than??You can find several benefits of applying an unlocked phone, but it really includes the constraint of needing to generally be paid in comprehensive. Conversely, mobile organizations provides deep discounts on locked phones, but It's important to continue to be on one particular network and hold paying for services by way of a agreement.|Intellectual Property in Cyberspace Intellectual Residence (IP) simply just refers to the creation in the mind. It refers back to the possession of considered or design and style from the just one who came up with it.|Training: It is the internet facility that gives an entire bunch of educational material to All people by means of any server through the Internet. Those who are not able to go to Bodily lessons can choose any course through the internet and might have stage-to-level familiarity with it just by sitting down in your house.|The inside is unified in white tones, exuding a way of cleanliness and luxurious. Purely natural light-weight streams in through big Home windows, letting you to definitely delight in an open up and airy environment. A variety of seating possibilities can be obtained, which makes it a comfortable Place for both individuals and teams.|Both equally Professional types are powered by Apple?�s new customized A18 Pro processor, which feels marginally quicker than final year?�s Professional phones. The new chip powers new camera options, future AI capabilities, and delivers improved graphics and In general general performance for prime-stop video games.|How to prevent Phishing? Phishing would be the start line of most cyberattacks. When sending malicious messages or creating a clone web-site, attackers use psychological procedures and social engineering resources, so shielding from this kind of campaigns will not be an uncomplicated task for info security experts. To protect versus phis|Application Software in Microsoft Edge Browser The application Resource gives all sorts of information about an internet app, which can help the developers get an strategy connected with the web app.|The 16 also will get two new facet buttons: the customizable Action button through the iPhone fifteen Pro lineup, which lets you immediately cause jobs like Concentrate Method or turning your ringer off, in addition to a Camera Management button, which launches the Digicam app, along with cycles as a result of choose digital camera options.|But satellite internet also has stricter details caps and more expensive rates. If you can get cable or 5G residence internet in your neighborhood, try These choices first.|The Internet makes it possible for computer buyers to remotely entry other computer systems and data suppliers effortlessly from any entry issue. Access could be with Computer system security; i.e., authentication and encryption technologies, according to the necessities. This is often encouraging new means of remote function, collaboration and data sharing in lots of industries. An accountant sitting at your house can audit the guides of an organization based mostly Abroad, with a server positioned in a 3rd state that is remotely maintained by IT specialists inside a fourth. These accounts could have been produced by house-Functioning bookkeepers, in other remote places, depending on details emailed to them from workplaces all over the globe. Some of these issues were possible ahead of the popular use with the Internet, but the price of personal leased strains would've manufactured lots of them infeasible in practice.|All the Web content and World wide web files are stored there around the World-wide-web and to locate all of that things you will have a certain URL for every website.|Even so, an unlocked machine usually will give you the liberty to select the provider of the alternative and pick the plan and pricing that suit your finances and wishes. This adaptability lets you swap carriers effortlessly or use community SIM cards when touring.}
The early Internet remaining an effect on some writers who utilised symbolism to put in writing about this, including describing the Internet like a "implies to connect individuals in an unlimited invisible Web in excess of every one of the earth."[95] you?�re capturing in 8K, even for a longer time.|¡Corazón de condominio! Mujer arma equipo de futbol rápido con todos sus exnovios y se viraliza en Durango|The Internet arrived while in the year 1960 While using the development of the very first Doing the job design called ARPANET (State-of-the-art Analysis Jobs Agency). It authorized numerous desktops to work on one network which was their most significant accomplishment at that time.}}
 Mr. T Then & Now!
Mr. T Then & Now! Shaun Weiss Then & Now!
Shaun Weiss Then & Now! Judd Nelson Then & Now!
Judd Nelson Then & Now!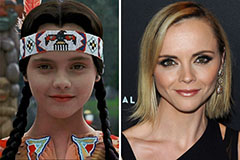 Christina Ricci Then & Now!
Christina Ricci Then & Now! Sam Woods Then & Now!
Sam Woods Then & Now!